Execution of The Operating System
Nonprocess Kernel
- Execute kernel outside of any process
- Operating system code is executed as separate entity that operates in privileged mode
- Own memory, own call stasck
- The concept of processes only applies to user programs
- All OS calls are blocking
Execute the kernel of the OS outside of any process (Figure 3.15a). With this approach, when the currently running process is interrupted or issues a supervisor call, the mode context of this process is saved and control is passed to the kernel.
OS has its own region of memory to use and its own system stack for controlling procedure calls and returns. The OS can perform any desired functions and restore the context of the interrupted process, which causes execution to resume in the interrupted user process.
Alternatively, the OS can complete the function of saving the environment of the process and proceed to schedule and dispatch another process.
OS code is executed as a separate entity that operates in privileged mode.
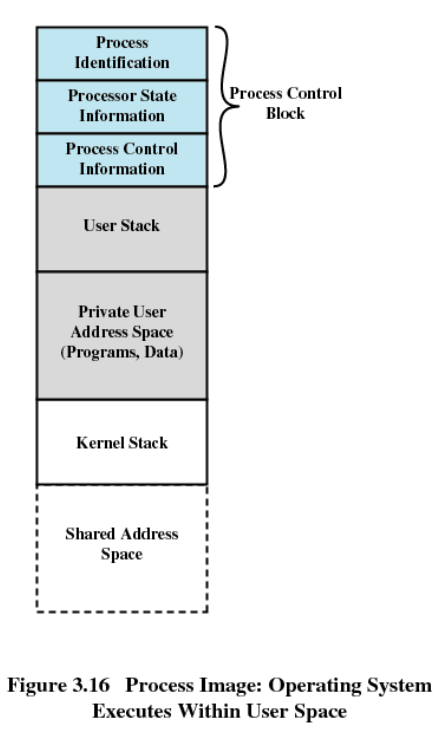
Execution within User Processes
- OS is primarily a collection of routines
- Operating system software within context of a user process
- Process executes in privileged mode when executing operating system code
- Perform a context switch (mode switch) when entering a system call, but continue with the same process.
Process-Based Operating System Implement the OS as a collection of system processes. In this case, major kernel functions are organized as separate processes.
Again, there may be a small amount of process- switching code that is executed outside of any process.
Useful in a multiprocessor or multicomputer environment, that is some of the operating system services can be shipped out to dedicated processors, improving performances